Why Australian Scouts is the Lifeline Your Screen-Addicted Child Needs Now
Is your child’s screen-addicted habit spiralling out of control? You’re not alone. Parents across Australia are grappling with the same issue. Hao Li’s scholarly article from Central South University reveals the urgent need for moderation and digital detoxification in children’s lives. The good news? Australian Scouts offers a proven, scholar-approved solution.
The Scholarly Warning
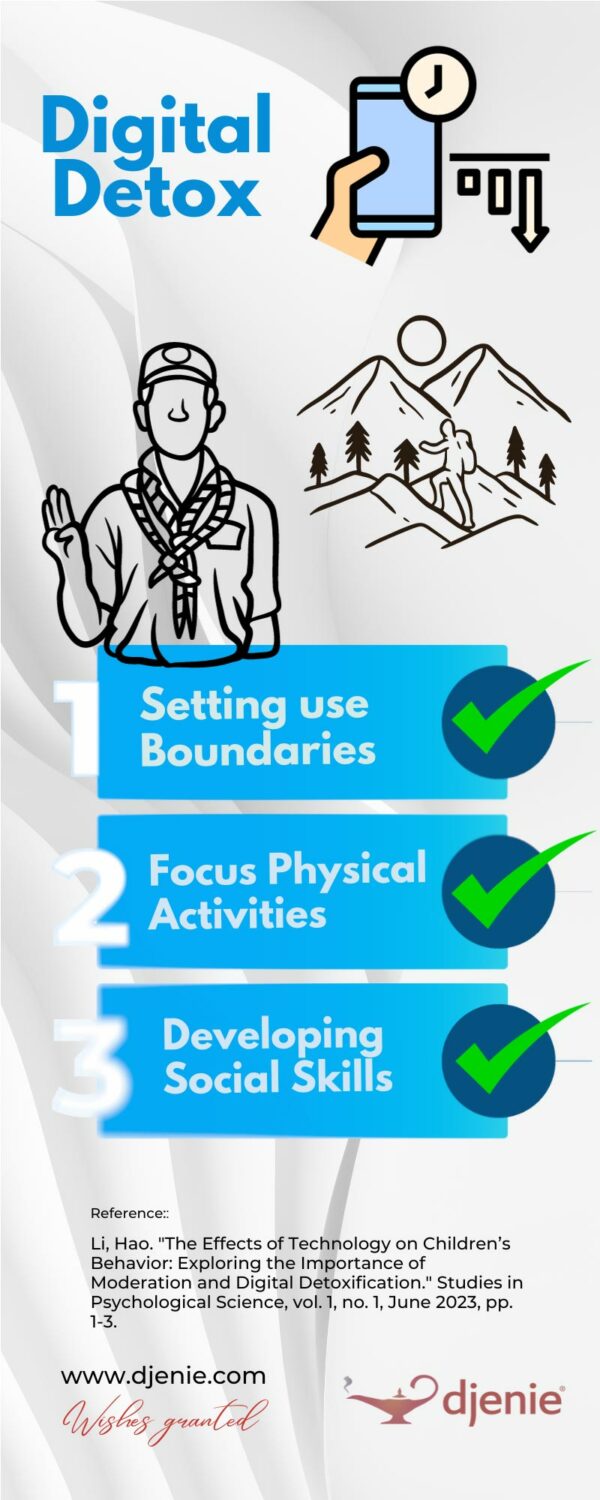
Hao Li’s groundbreaking article, “The Effects of Technology on Children’s Behavior: Exploring the Importance of Moderation and Digital Detoxification,” warns that excessive technology use can lead to detrimental effects on a child’s physical health, social skills, academic performance, and mental well-being. The article strongly advocates for setting boundaries on screen time and encouraging outdoor activities as a form of digital detox.
Why Australian Scouts?
Australian Scouts is not just another extracurricular activity; it’s a lifeline for your child in this digital age. With a rich history and a focus on outdoor activities, community service, and skill development, Australian Scouts directly addresses the scholarly recommendations for digital detoxification and moderation.
Download This Infographic In PDF Format!
The Aussie Context
In Australia, the allure of screens is even more potent due to our highly urbanized lifestyle. This makes the outdoor focus of Australian Scouts not just beneficial but essential. It offers kids a rare chance to connect with Australia’s unique natural environment.
Why Outdoor Activities Are Non-Negotiable
According to Hao Li, outdoor activities are essential for counteracting the negative effects of excessive screen time. They promote physical health and social interaction, which are crucial for a child’s development. Australian Scouts offers activities like bushwalking, camping, and sailing that are not only fun but also incredibly beneficial for your child’s well-being.
Scouting’s Role in Digital Detox
- Setting Boundaries: Australian Scouts naturally limits screen time, aligning perfectly with Hao Li’s scholarly advice.
- Boosting Physical Activity: The outdoor focus of Australian Scouts ensures that your child is physically active, which is crucial for their physical health.
- Enhancing Social Skills: Scouts promotes face-to-face interaction, a key factor in social development, as emphasized by Hao Li.
The Australian Scouts Advantage
What sets Australian Scouts apart is its commitment to fostering a sense of community and citizenship. It’s not just about individual growth; it’s about growing together as responsible members of society. This aligns with Hao Li’s emphasis on fostering social interaction as a counter to screen-induced isolation.
Don’t let screens dictate your child’s life. Give them the balanced, healthy life they deserve. Enroll them in Australian Scouts today and watch them transform into confident, responsible, and happy individuals.
Glossary of Key Terms from Hao Li’s Article
-
- Moderation: The act of avoiding excess or extremes, especially in terms of screen time.
- Digital Detoxification: A period of time during which a person refrains from using electronic devices.
- Physical Health: The overall condition of an individual’s body.
- Social Skills: The skills we use to communicate and interact with each other.
- Academic Performance: How well a student is accomplishing their academic goals.
- Mental Well-being: The state of being comfortable, healthy, or happy in terms of mental health.
REFERENCE
DISCOVER MORE POSTS
Explore
ENJOYED THIS POST?
Follow us on social media to stay up-to-date with our latest posts
JOIN THE CONVERSATION!
Let’s Make It Meaningful Together





