Cybersecurity And Xero Trust, Mitigate The Threats!
THE PATH TO A ‘ZERO TRUST’ SECURITY MODEL
In the expanding digital landscape that Scouts Australia navigates, the importance of robust cybersecurity models has never been more crucial, believe me with 20 years in this business the importance of adopting accepted model has never been greater. Simply read the new and you’ll soon be put in the grim picture; utilise tested methods. A standout model is the Zero Trust security model. This model revolves around a straightforward yet impactful principle: “Never trust, always verify.” This is principle we embrace here at Djenie, and that should be comforting for you as we have access to your children’s data. Here’s a glimpse into five persuasive reasons why Scouts Australia should consider embracing Zero Trust to enhance its cybersecurity posture.
Download This Infographic In PDF Format!
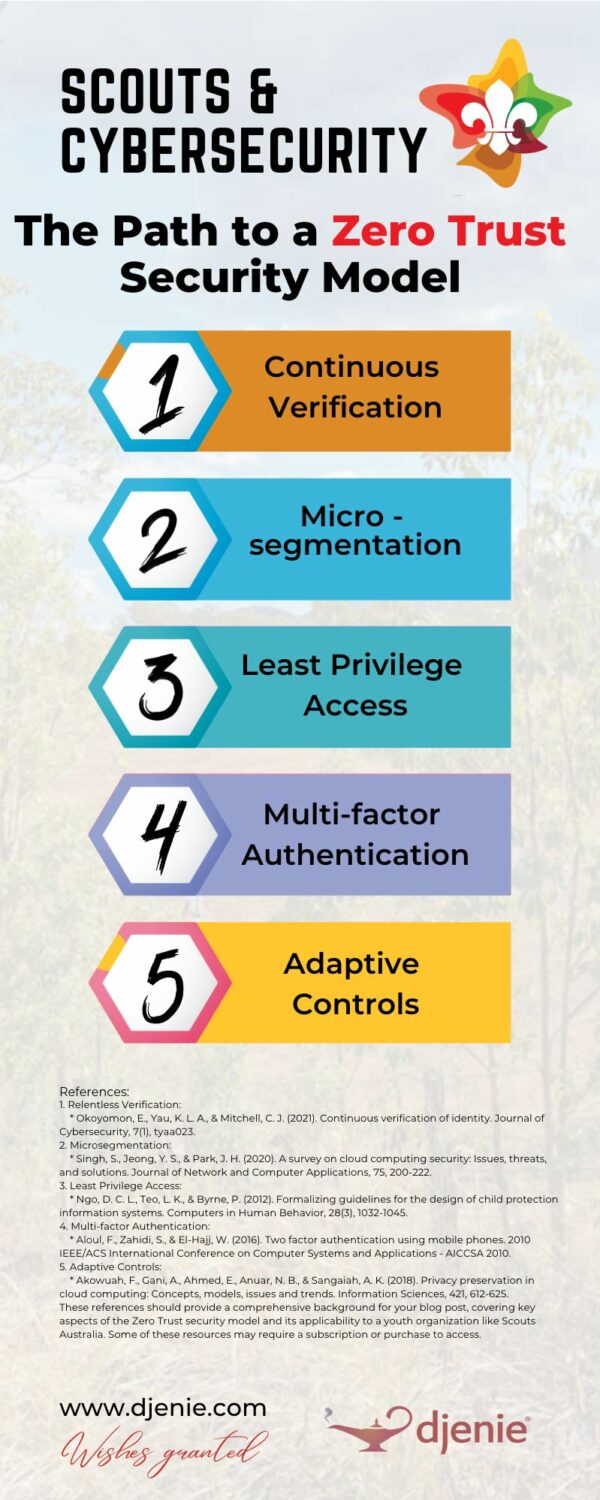
Relentless Verification:
Zero Trust treats every user, device, and system as a potential threat. It validates and authenticates every request, no matter its source, creating a persistent security layer.
Microsegmentation:
Zero Trust utilises microsegmentation, a strategy that breaks a network down into smaller, isolated segments. This method prevents lateral movement within the network, significantly limiting the potential damage if a breach occurs.
Least Privilege Access:
Zero Trust aligns with the Principle of Least Privilege (PoLP), affording users only the access essential for their tasks. This approach minimises the risk of internal threats and privilege misuse.
Multi-factor Authentication:
Typically, Zero Trust models incorporate multi-factor authentication, adding an additional layer of security. This helps verify a user’s authenticity before granting access.
Adaptive Controls:
Zero Trust adopts adaptive risk controls that adjust based on the situation. If unusual behaviour is detected, access is immediately restricted or denied.
In a time where data breaches are worryingly frequent, the Zero Trust security model provides a proactive means to protect valuable information. It’s not about being pessimistic, but rather being pragmatic and secure in a world where data protection is vital. Djenie’s genies are certainly not pessimistic, nor cantankerous, difficult to deal with nor a pain. We are quite delightful to deal with actually.
We welcome your thoughts on the Zero Trust security model. Has your organisation, perhaps even your Scout group, implemented it? Share your experiences and insights in the comments below. And remember, for more invaluable cybersecurity insights, subscribe to our newsletter today!
Make sure you check out our other posts below on this important topic of Data Security and please let us know if you find that helpful too. Thanks for reading. Say safe.
REFERENCE
1. Relentless Verification:
- Okoyomon, E., Yau, K. L. A., & Mitchell, C. J. (2021). Continuous verification of identity. Journal of Cybersecurity, 7(1), tyaa023.
- Australian Cyber Security Centre. (2022). Essential Eight. https://www.cyber.gov.au/resources-business-and-government/essential-cyber-security/essential-eight
2. Microsegmentation
- Singh, S., Jeong, Y. S., & Park, J. H. (2020). A survey on cloud computing security: Issues, threats, and solutions. Journal of Network and Computer Applications, 75, 200-222.
3. Least Privilege Access
- Ngo, D. C. L., Teo, L. K., & Byrne, P. (2012). Formalizing guidelines for the design of child protection information systems. Computers in Human Behavior, 28(3), 1032-1045.
4. Multi-factor Authentication:
- Aloul, F., Zahidi, S., & El-Hajj, W. (2016). Two factor authentication using mobile phones. 2010 IEEE/ACS International Conference on Computer Systems and Applications – AICCSA 2010.
5. Adaptive Controls
- Akowuah, F., Gani, A., Ahmed, E., Anuar, N. B., & Sangaiah, A. K. (2018). Privacy preservation in cloud computing: Concepts, models, issues and trends. Information Sciences, 421, 612-625.
DISCOVER MORE POSTS ABOUT
Child Wellbeing & Security
ENJOYED THIS POST?
Follow us on social media to stay up-to-date with our latest posts
JOIN THE CONVERSATION!
Let’s Make It Meaningful Together






















