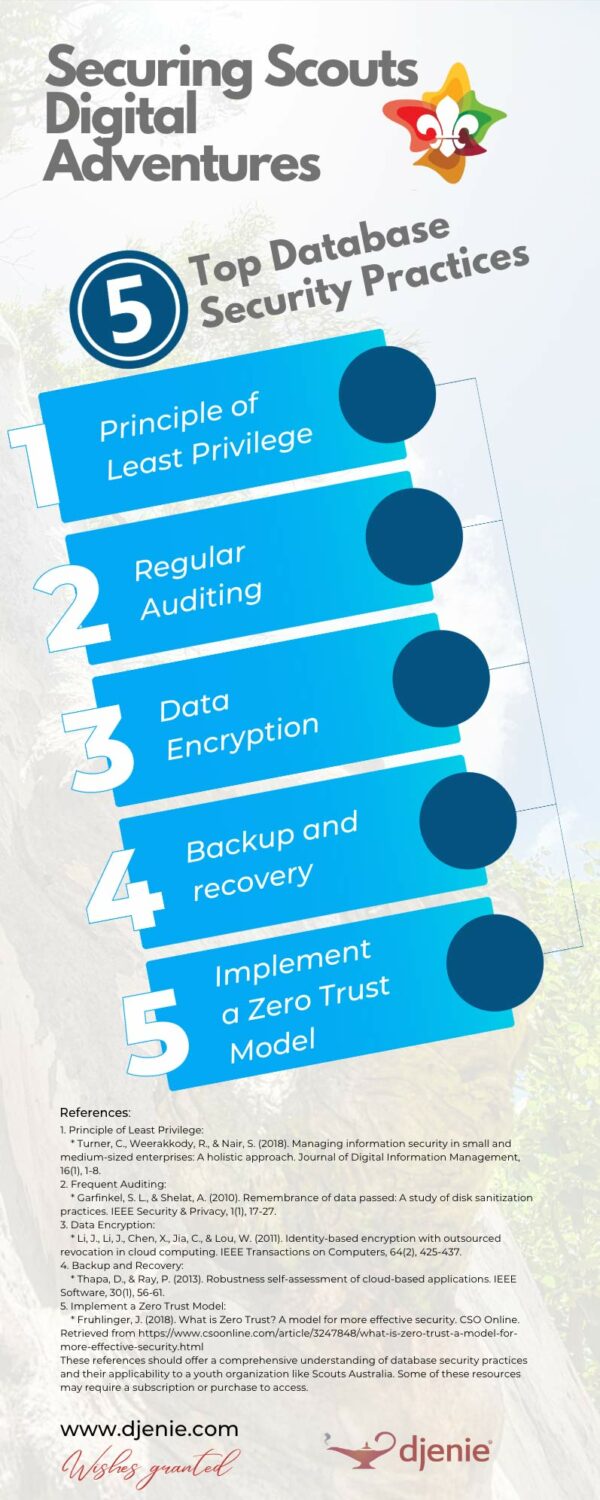
The 5 Top Database Security Practices You Must Follow
SECURING SCOUTS DIGITAL ADVENTURES
Download This Infographic In PDF Format!
Principle of Least Privilege:
Embrace the Principle of Least Privilege (PoLP), much like you would restrict access to the scoutmaster’s tent. Grant users only the necessary access levels to perform their duties, reducing the risk of internal threats and unauthorized access.
Frequent Auditing:
Regularly inspect your database just as you would a campsite, to spot potential security gaps. Monitor user activities, changes to database structures, and unusual usage patterns to detect any potential threats early.
Data Encryption:
Encrypt your data, both at rest and in transit, to make it unreadable to unauthorized users, much like a secret scout code. This is a crucial line of defense in case of a breach, as it renders stolen data useless without the decryption keys.
Backup and Recovery:
Regularly back up your data and have a solid recovery plan in place, similar to having an emergency evacuation plan. In case of a data loss event, this ensures you can restore your system to its previous state with minimal downtime.
Implement a Zero Trust Model:
Treat every request as a potential threat, much like a suspicious noise in the bush during a night hike. Always verify the identity and permissions of users requesting access, regardless of whether the request originates from inside or outside the network.
By following these database security best practices, Scouts Australia can establish a strong defense against potential threats, minimizing the risk of data breaches and ensuring that operations run as smoothly as a well-organised scout jamboree.
How are you managing database security within your organization? We’d love to hear about your experiences and insights in the comments below. And if you haven’t yet, subscribe to our newsletter for more indispensable cybersecurity insights! Stay safe and prepared, Scouts!
Discover More: A Direct Insight
REFERENCES
These references should offer a comprehensive understanding of database security practices and their applicability to a youth organization like Scouts Australia. Some of these resources may require a subscription or purchase to access.
1. Principle of Least Privilege
- Turner, C., Weerakkody, R., & Nair, S. (2018). Managing information security in small and medium-sized enterprises: A holistic approach. Journal of Digital Information Management, 16(1), 1-8.
2. Frequent Auditing:
- Garfinkel, S. L., & Shelat, A. (2010). Remembrance of data passed: A study of disk sanitization practices. IEEE Security & Privacy, 1(1), 17-27.
3. Data Encryption:
- Li, J., Li, J., Chen, X., Jia, C., & Lou, W. (2011). Identity-based encryption with outsourced revocation in cloud computing. IEEE Transactions on Computers, 64(2), 425-437.
4. Backup And Recovery:
- Thapa, D., & Ray, P. (2013). Robustness self-assessment of cloud-based applications. IEEE Software, 30(1), 56-61.
5. Implement a Zero Trust Model:
- Fruhlinger, J. (2018). What is Zero Trust? A model for more effective security. CSO Online. Retrieved from https://www.csoonline.com/article/3247848/what-is-zero-trust-a-model-for-more-effective-security.html
- UpGuard. (2022, August 15). The Biggest Data Breaches in Australia. UpGuard. https://www.upguard.com/blog/biggest-data-breaches-australia
- Medibank. (2023). Cyber security. Medibank. https://www.medibank.com.au/health-insurance/info/cyber-security/mhh/
DISCOVER MORE POSTS ABOUT
Child Wellbeing & Security
ENJOYED THIS POST?
Follow us on social media to stay up-to-date with our latest posts
JOIN THE CONVERSATION!
Let’s Make It Meaningful Together






















