More Security Is Needed, Harden Your Database!
THAT’S WHAT IS NEEDED FOR REAL SECURITY
Download This Infographic In PDF Format!
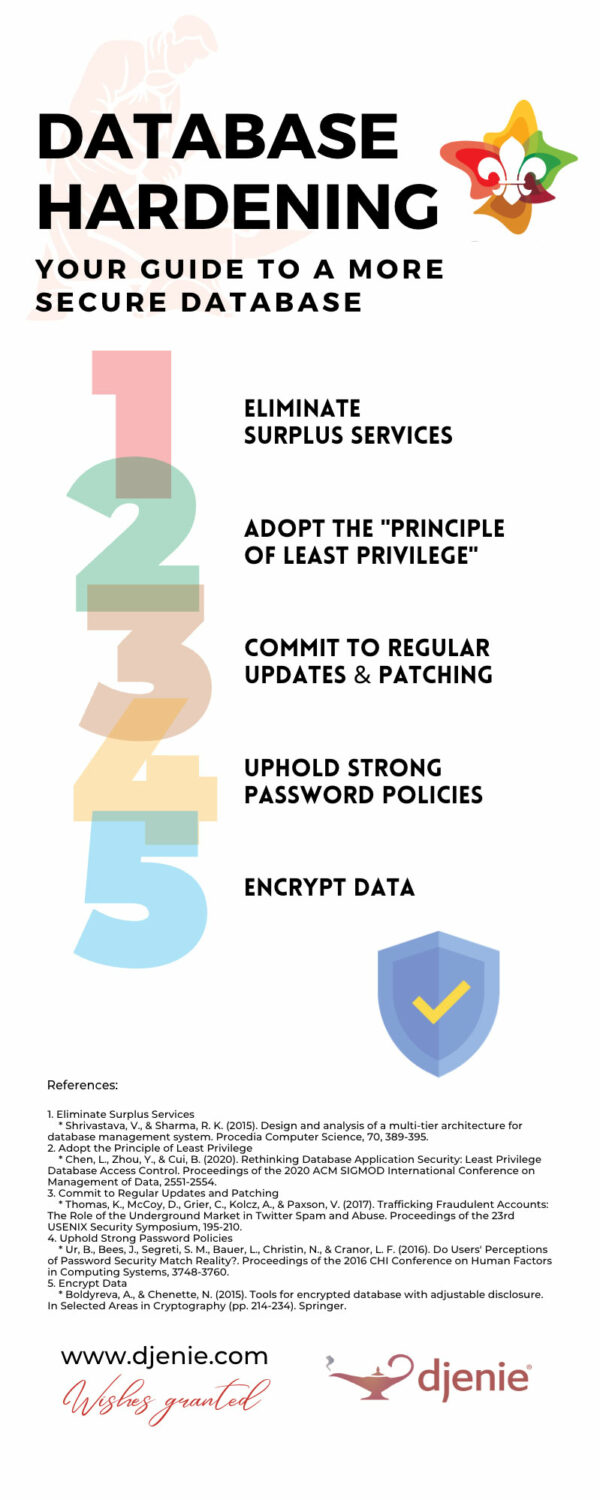
Eliminate Surplus Services:
Much like clearing unnecessary items from our camping gear, databases often come with additional services that you may not need. Removing or disabling these reduces potential entry points for vulnerabilities.
Adopt the Principle of Least Privilege:
This principle aligns with your scout motto, “Be Prepared.” Grant users ONLY the access they need for their roles, reducing the risk of unauthorised data manipulation.
Commit to Regular Updates and Patching:
Just as you keep your scout gear well-maintained, you should ensure your database software is always updated. Regularly install patches to fix known vulnerabilities and keep the database at its safest.
Uphold Strong Password Policies:
Implement the use of complex, unique passwords and encourage regular changes. This practice is akin to securing your tent zips against unwanted intruders.
Encrypt Data:
Secure your data at rest and during transmission. If a breach does occur, encryption ensures that stolen data remains unreadable without the decryption keys, much like a secret scout code.
By following these database hardening practices, you can significantly reduce your digital campsite’s exposure to potential cyber threats. Remember, securing your database isn’t just about protecting data—it’s also about upholding the trust and reputation of Scouts Australia.
Have you got other insights about hardening databases in an AI-dominated world? Share your thoughts and experiences in the comments below. And remember, for more tips on cybersecurity, subscribe to our newsletter today! Let’s continue to make our digital world a safer place for all scouts.
Make sure you check out our other posts below on this important topic of Data Security and please let us know if you find that helpful too. Thanks for reading. Say safe.
REFERENCES
1. Eliminate Surplus Services
- Shrivastava, V., & Sharma, R. K. (2015). Design and analysis of a multi-tier architecture for database management system. Procedia Computer Science, 70, 389-395.
2. Adopt the Principle of Least Privilege
- Chen, L., Zhou, Y., & Cui, B. (2020). Rethinking Database Application Security: Least Privilege Database Access Control. Proceedings of the 2020 ACM SIGMOD International Conference on Management of Data, 2551-2554.
3. Commit to Regular Updates and Patching
- Thomas, K., McCoy, D., Grier, C., Kolcz, A., & Paxson, V. (2017). Trafficking Fraudulent Accounts: The Role of the Underground Market in Twitter Spam and Abuse. Proceedings of the 23rd USENIX Security Symposium, 195-210.
4. Uphold Strong Password Policies
- Ur, B., Bees, J., Segreti, S. M., Bauer, L., Christin, N., & Cranor, L. F. (2016). Do Users’ Perceptions of Password Security Match Reality?. Proceedings of the 2016 CHI Conference on Human Factors in Computing Systems, 3748-3760.
5. Encrypt Data
- Boldyreva, A., & Chenette, N. (2015). Tools for encrypted database with adjustable disclosure. In Selected Areas in Cryptography (pp. 214-234). Springer.
DISCOVER MORE POSTS ABOUT
Child Wellbeing & Security
ENJOYED THIS POST?
Follow us on social media to stay up-to-date with our latest posts
JOIN THE CONVERSATION!
Let’s Make It Meaningful Together